Transforming Smartphones into Hardware Wallets with Secure Enclave on Flow

Secure Enclave enhances the security of mobile applications and protects user data from unauthorized access to devices. While it's common for things like credit cards and transit passes to be secured by the hardware in phones, crypto wallets have not yet leveraged this powerful security resource.
On Flow, crypto wallets can use Secure Enclave to provide security on par with hardware wallets without compromising on accessibility and convenience. These wallets can be fully customized to support different types of recovery mechanisms.
Wallets are the first touch point for new users, and lowering the barrier to entry without compromising on security helps expedite web3 adoption for the entire web3 ecosystem. This article explains how Flow provides unmatched Secure Enclave support for building wallets.
What is a Secure Enclave?
A Secure Enclave is a hardware-based security feature available on modern devices, like smartphones, tablets, or laptops. It provides a high level of security by preventing unauthorized access to sensitive data such as cryptographic keys, passwords, and biometric data. It protects the cryptographic keys both while they are being stored and while they are being used and ensures data integrity through tamper resistance and access controls.
Secure Enclaves are implemented via dedicated security chips in the device known as a secure element (or Trusted Execution Environment) that runs code using sensitive data. To ensure that sensitive data remains protected even if the main operating system is compromised, the Secure Enclave is kept isolated and insulated from the main processor and the rest of the system.
(Note that “Secure Enclave” is the preferred term used by Apple for hardware-based security features. Modern Android, Windows and Linux devices provide equivalent hardware-based security but refer to it using other terms. In this article, we refer to all of these hardware security features as “Secure Enclave”.)
What does Secure Enclave mean for web3?
In web3, a user’s account is secured by the keys they own. Losing your keys means losing access to your web3 account, and therefore losing access to all your onchain assets. Users generally delegate crypto wallets with tasks concerning authorized access and key security.
A new user’s journey typically starts with a custodial software wallet also known as a hosted wallet. For example, when a user creates an account on coinbase.com, Coinbase creates a hosted wallet for the user in the background. Custodial wallets take on the burden of securing a user's accounts and assets for them. As users become more experienced in web3, and conscious of achieving “true ownership” of their accounts and assets, they typically begin using a self-custodial software or hardware wallet that stores their keys.
How do software and hardware wallets fall short?
While self-custodial software and hardware wallets are popular choices for mature crypto users, they both have several shortcomings.
Shortcomings of Software Wallets
- Since software wallets are accessible online, they are vulnerable to hacking, malware, phishing attacks, and other forms of cybercrime.
- If the device (e.g., smartphone or computer) hosting the wallet is compromised (through malware, viruses, or physical theft), the wallet and its assets can be at risk.
- Unlike custodial wallets, self-custodial software wallets typically do not offer recovery options if private keys are lost, making the stakes higher for users.
Shortcomings of Hardware Wallets
Hardware wallets are not accessible online and hence eliminate the risk of online attacks, but they too have their fair share of disadvantages.
- Hardware wallets are inconvenient for frequent transactions — imagine trying to play a web3 game where every other interaction requires a transaction to be submitted. The user would have to repeatedly press the buttons on the hardware wallet for each transaction, completely undermining the user experience of the game.
- They almost always have a way to export the key, which means there is always the potential for a back door from the manufacturer.
- They require users to manually store and secure the exported seed phrase outside of their wallet — potentially undermining all the benefits of using a hardware wallet.
- Similar to software wallets, there is no form of recovery if the private keys are lost.

Overall, Software and hardware wallets also do not promote good security hygiene as users of these wallets often copy the exported keys of their account from one device to another as a way to mitigate the risk of losing the keys and for the convenience of having multiple wallets initialized with the same keys.
Secure Enclave wallets offer the best of both worlds
Unlike hardware wallets, Secure Enclave wallets do not require a separate device and can run on most devices (such as a phone or a laptop that includes a secure element). Thus, Secure Enclave wallets effectively convert the user’s existing device into a hardware wallet. This leap in accessibility and convenience makes frequent transactions easy, and key access can be done through biometrics without compromising security.
Unlike a software wallet or a hardware wallet, a secure enclave for both Apple and Android does not allow exporting of the unencrypted key and the keys are forever tied to the device.
By combining the accessibility and convenience of a software wallet with the security of a hardware wallet, Secure Enclave emerges as the best choice for a crypto wallet. However, there are a few disadvantages which have slowed down its adoption in web3:
- Onchain support is unavailable: While most devices support a Secure Enclave, not all wallets running on those devices can leverage that functionality. For a wallet to support a Secure Enclave, the chain protocol must support one of the algorithms or curves supported by the enclave, including the NIST P-256 curve (also known as secp256r1 or prime256v1), as part of its account signatures.
- No account recovery: Since the keys in the Secure Enclave are tied to the device, if the device is lost, the private keys stored in its Secure Enclave will also be lost, permanently compromising your ability to access your accounts and data.
Fortunately, the account model on Flow lets the wallet developer overcome both of these disadvantages.
How does a Secure Enclave work on Flow?
Native support for NIST P-256
Flow has native support for the industry-standard NIST P-256 elliptic curve (also known as secp256r1) used in secure enclaves. This inbuilt support unburdens the wallet developer and allows them to build secure enclave wallets on Flow with minimal effort.
To use Secure Enclave on Flow blockchain, wallet developers can use the CryptoKit framework on iOS and the Keystore system on Android. Flow Wallet demonstrates how to use Secure Enclave with Flow.
The availability of Secure Enclave wallets means that web3 applications using these wallets on Flow are inherently more secure, accessible and easy to use.
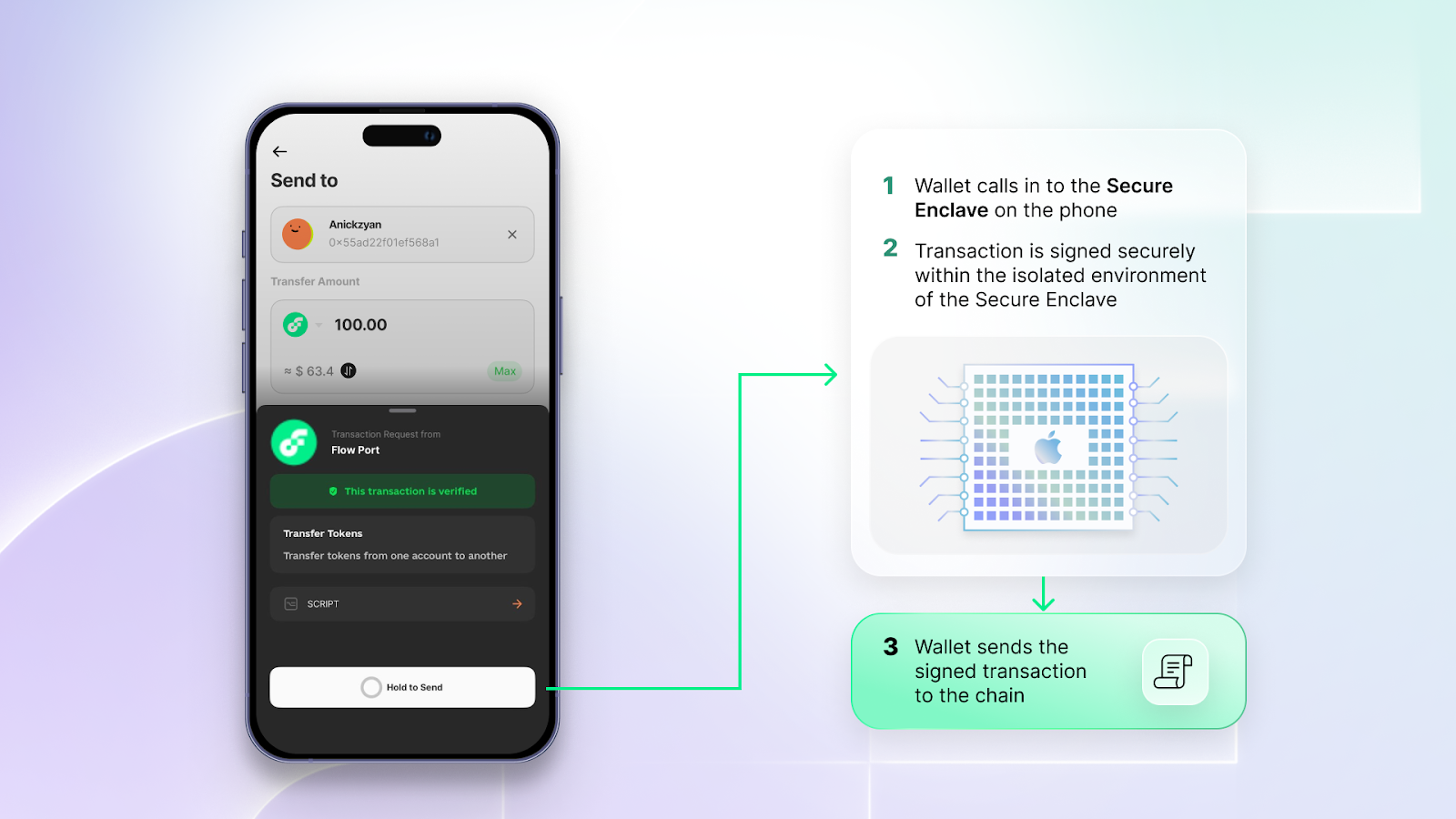
Compare this to popular chains like Ethereum and Bitcoin, which do not support NIST P-256 natively. Consequently, cryptocurrency wallet mobile apps on these chains use main-processor signing instead of secure-element signing. Signing in the main processor is vulnerable to hardware attacks that leak information about the private key. Today, chains like Ethereum are being retrofitted via smart contracts to support P-256 (e.g. RIP 7212), but this introduces performance overhead, security risks, complexity, interoperability issues, and overall degraded user experience due to higher gas cost and transaction delays.
Secure Enclave support on EVM
With Flow EVM, support for a Secure Enclave extends to EVM. Flow EVM allows a user's EVM addresses to be controlled by a Cadence account secured with Secure Enclave. This means a user can send and receive EVM assets and use EVM contracts using the hardware security of devices they already own.
Easy account recovery
Flow overcomes one of the biggest challenges end-users face with a Secure Enclave: if you lose your device, you have lost your account.
The native account abstraction model on Flow fixes this by decoupling addresses from private keys, allowing users and wallets to add multiple keys with varying signing power expressed as key weights to the same account. This approach provides greater flexibility and security in key management while also reducing the risk of losing access to private keys.
The same account can have multiple keys stored in different devices — if one device is lost, the account is still accessible via the other keys.
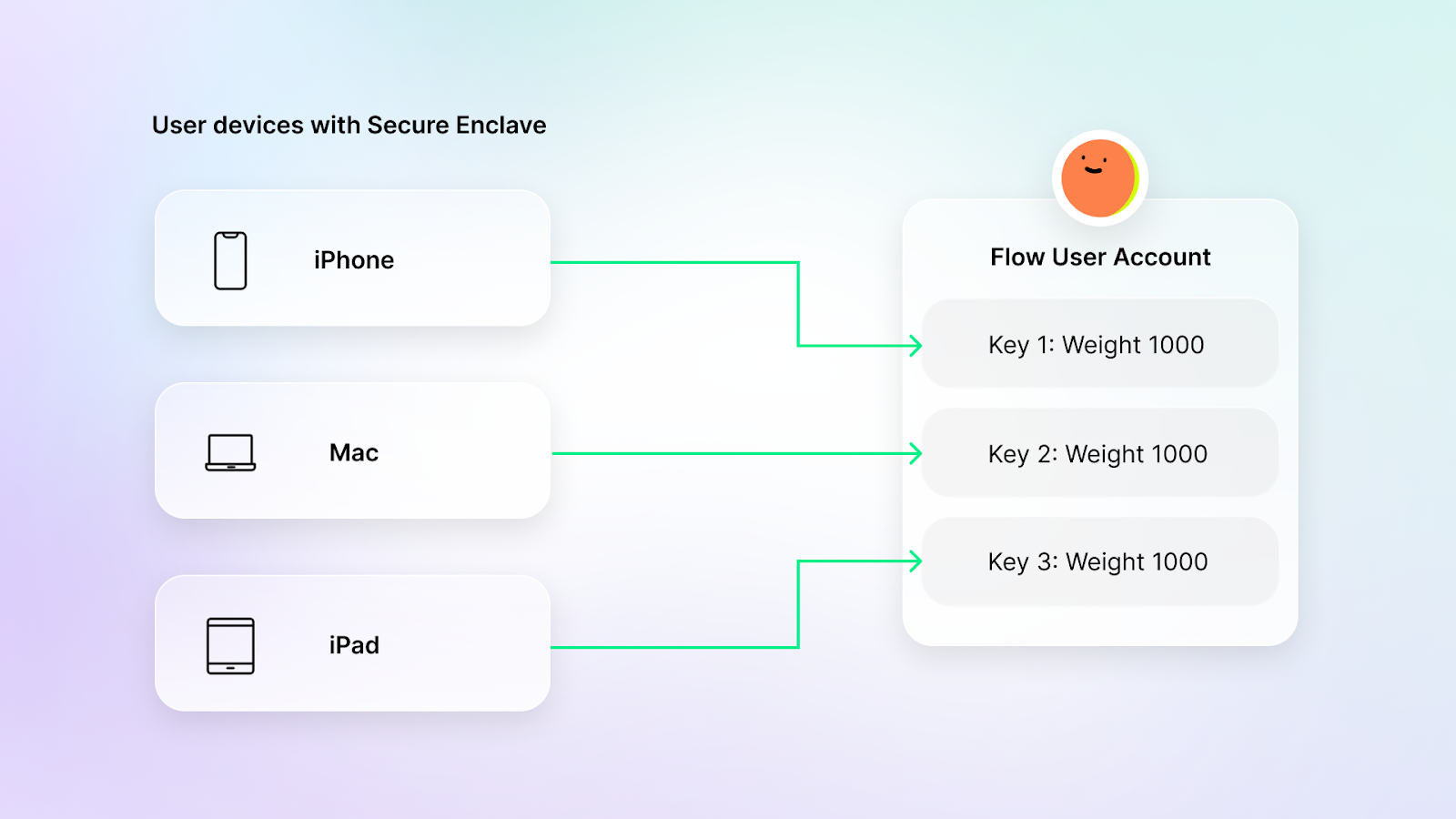
Security Enclave can be used in combination with other key management techniques (such as Cloud-based HSM) to store a two-of-two, or some other combination of multi-sign backup keys.

Compare this with Externally Owned Account (EOA) on Ethereum, which only allows a single key natively, and account abstraction has to be built on top (ERC-4337). Such a non-native solution comes with its own challenges regarding security, complexity, and transaction cost.
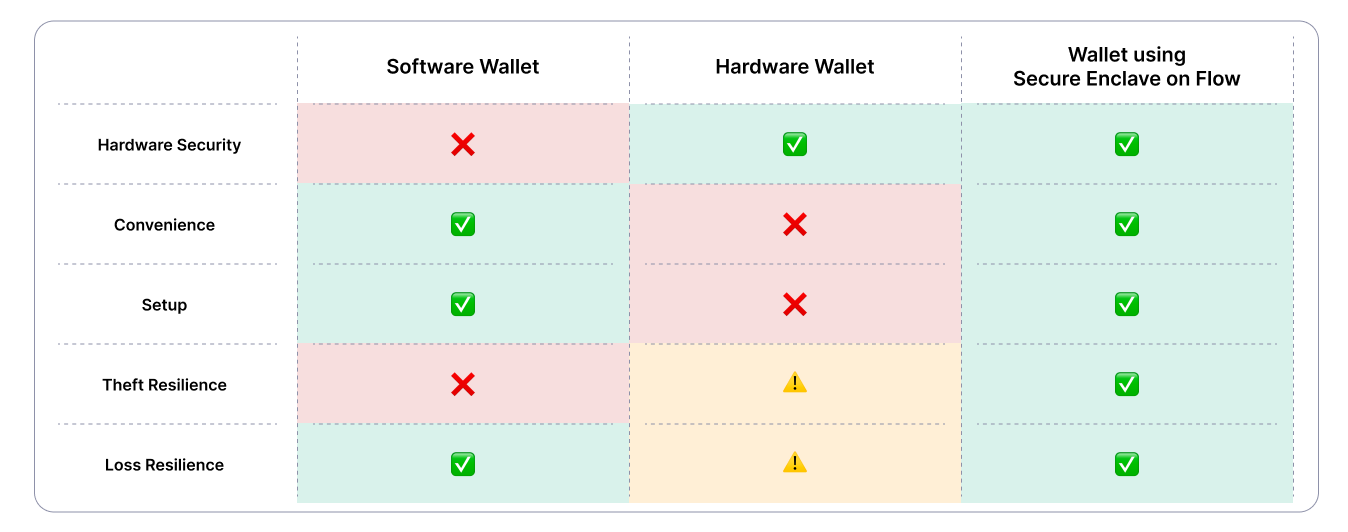
Here is a quick summary on how the different wallets compare with each other:
Account recovery through account linking
Building on the account model, the Flow-native account linking feature offers additional account recovery support.
A wallet owner’s accounts can be linked to their main account (i.e. a child-to-parent account). If an owner loses access to the keys that control their child accounts, they can still withdraw and manage the child account’s assets by executing transactions with the parent account.
Next-gen social recovery
In addition to the account model, Cadence, the native programming language of Flow, also provides some unique possibilities for developers to create onchain account recovery mechanisms. Onchain Decentralized Autonomous Organizations (DAOs) can be created that have the authority to set keys on a wallet owner’s account should they lose access to their existing keys. A wallet owner could also programmatically grant the right to set keys on their account to a trusted friend.
Secure Enclave-based Smart Wallets
Smart Wallets (also known as Smart Contract Wallets) that support Passkeys are one of the latest trends in web3. Passkeys are a replacement for passwords. But unlike passwords, where a user has to provide credentials to authenticate, a Passkeys’ credentials are stored on the device within the Secure Enclave, and a user only has to prove ownership of the device via biometrics to use those credentials to authenticate (e.g. logging into a bank account by just scanning your fingerprint on the phone versus punching in a password). Another important aspect of Passkeys is that the credentials are synced across all user devices and the cloud. For example, in the case of Apple devices, Passkeys sync across a user's devices using iCloud Keychain; in the case of Android, Google Password Manager does the same between all Android devices of the user.
Regular hardware and software wallets cannot use Passkeys directly since, as we have seen, Secure Enclave based keys require the chain to support a special NIST P-256 elliptic curve. Hence a new class of crypto wallets have emerged, especially on Ethereum, called Smart Wallets, which leverage Passkeys via the combination of ERC-4337 (Account Abstraction) and RIP 7212, which provides onchain secp256r1 signature verification. However, a major drawback of such a smart contract based Smart Wallet is that the transactions submitted through such a wallet utilize a lot of onchain computations, first for the account abstraction layer and then for the signature verification. Subsequently, the transaction ends up being very costly in terms of gas fees. For a simple eth transfer transaction on Ethereum, account abstraction alone costs four times more gas as compared to a simple EOA-to-EOA transfer.
Here too, Flow’s native support for secure enclave helps build a superior Smart Wallet solution with Passkeys that do not incur any additional processing overhead and hence reduce complexity and costs.
Conclusion
Flow offers built-in support for the NIST P-256 curve and easy account recovery, enabling wallet developers to use the Secure Enclave technology to create wallets that enhance user experience while also enhancing security—two factors that generally are in conflict. These wallets in turn will help usher in the next wave of web3 applications.


















